The rising threats of IoT devices to election, healthcare, and energy infrastructure
Internet of Things (IoT) devices such as fitness trackers and home security cameras are growing in popularity, but many people don’t realize that these devices can also be used to attack critical infrastructure. In 2017, a group of hackers used IoT devices to launch a massive attack on the internet infrastructure provider Dyn, and they were only able to do this because they were able to exploit devices that were using default passwords.
Defense-in-Depth: A Multi-Layered Cybersecurity Approach
As the world becomes increasingly digitized, the risk of cyberattacks against businesses, governments, and individuals alike has increased dramatically. Hackers can gain access to sensitive data, steal identities or financial information, or damage computer networks and critical infrastructure.
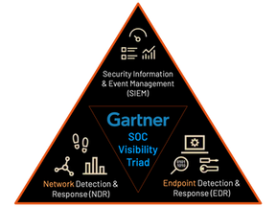
EDR and NDR
Two of the most important aspects of cybersecurity are network detection and response (NDR) and endpoint detection and response (EDR). While on the surface, there may appear to be similarities between the two, there are some key differences.