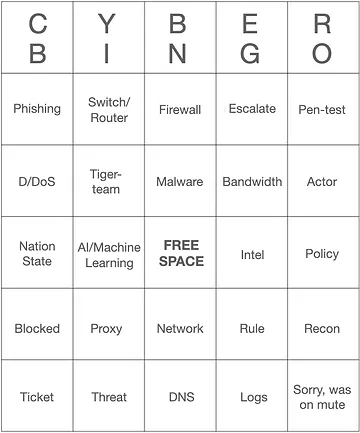
| Phishing | Spear phishing or regular works |
| SwitchA networking switch is a device that connects multiple devices on a computer network, using hardware addresses to process and forward data to the intended destination. Switches operate at the data link layer of the OSI model and can create a network of interconnected devices, offering efficient and direct data paths.
See More...
See Less...
/RouterA networking device that forwards data packets between computer networks, determining the best path for each packet based on its destination IP address.
See More...
See Less...
| Switch or router-type infrastructure. HubA basic networking device that connects multiple devices in a Local Area Network (LAN), sending data received from one device to all other devices.
See More...
See Less...
would also be a valid entry |
| Firewall | A vendor brand such as Palo-Alto, or Cisco works as long as it is within the context of a firewall |
| Escalate | The exact word needs to be used |
| Pen-test | Pen-testing or red-team can be considered valid entries |
| D/DoS | "Distributed denial of serviceA cyber-attack in which multiple compromised computer systems attack a target, such as a server, website, or network, and cause a denial of service for users of the targeted resource. The flood of incoming messages from many sources overwhelms the target, rendering it inaccessible.
See More...
See Less...
" or just "denial of serviceA cyber-attack where a perpetrator seeks to make a machine or network resource unavailable to its intended users by temporarily or indefinitely disrupting services of a host connected to the internet. Unlike a DDoS attack, a DoS attack typically originates from a single source.
See More...
See Less...
" are valid |
| Tiger-team | Can be used singular or plural |
| MalwareSoftware that is specifically designed to harm or exploit any computer, network, service, or program.
See More...
See Less...
| Malware, RansomwareA type of malicious software designed to block access to a computer system or data, typically by encrypting it, until a sum of money is paid. Ransomware attacks can affect individuals, businesses, and government agencies, leading to significant data loss and financial damage.
See More...
See Less...
, or the type of actual name of the malware are valid to complete this square |
| BandwidthThe capacity for transmitting data over a network connection or circuit, measured in bits per second. It indicates the maximum rate at which data can be sent, impacting the speed and efficiency of data transmission.
See More...
See Less...
| As it refers to networkA collection of interconnected computers, servers, and other devices that allow for the exchange and sharing of data and resources. Networks can be classified based on size, function, and access. Common types include Local Area Network (LAN), which connects devices in a localized area such as an office or home; Wide Area Network (WAN), which connects devices across large distances, possibly globally; and Virtual Private Network (VPN), which provides secure, encrypted connections over the internet. A network relies on standardized protocols, such as TCP/IP, to ensure uniform communication and data transfer between devices.
See More...
See Less...
traffic, or available time to work on something (not the circumference of musicians) |
| Actor | Used in the form of a threat actor, not the actor seen in a movie or TV show |
| Nation-stateIn the context of cybersecurity, a nation-state refers to the involvement of national governments in cyber attacks or cyber espionage. These entities may engage in hacking to conduct espionage, influence geopolitics, or achieve strategic objectives, often using sophisticated methods and advanced technology.
See More...
See Less...
| Must be both words used (Nation-state) to complete the square. Using 'nation' on its own and then later using
'state' doesn't count |
| Al/Machine LearningMachine Learning is a subset of artificial intelligence (AI) focused on building systems that learn from data. It enables computers to improve their performance on a specific task with data, without being explicitly programmed. This involves algorithms that can identify patterns, make decisions with minimal human intervention, and predict outcomes based on historical data.
See More...
See Less...
| Any variants of Artificial intelligenceA branch of computer science that focuses on creating systems capable of performing tasks that typically require human intelligence. These tasks include learning, reasoning, problem-solving, perception, and language understanding. AI can be categorized into narrow or weak AI, which is designed for specific tasks, and general or strong AI, which has the capability of performing any intellectual task that a human being can.
See More...
See Less...
or machine learning are valid entries; this also includes terms such as supervised or unsupervised neural networksUnsupervised neural networks are designed to learn hidden patterns and structures from unlabeled data, typically used for clustering or associating different inputs.
See More...
See Less...
|
| Free Space | It doesn't need to be said, but if someone says it, then you know that you're on a roll with this group! |
| Intel | It is intended in the context of threat intelligenceEvidence-based knowledge about an existing or emerging threat or hazard that can be used to inform decisions regarding the threat's mitigation or response.
See More...
See Less...
, not the computer chip maker. However, you could still complete the square and argue the processIn computing, a process is an instance of a computer program that is being executed. It contains the program code and its current activity. Each process has a unique process ID and maintains its own set of resources such as memory and processor state. A process can initiate sub-processes, creating a tree of processes.
See More...
See Less...
|
| Policy | Policy, as it relates to business or rule policy, is fine. You may want to agree beforehand if anything from governance is allowed to complete this square, such as NISTA U.S. Department of Commerce agency that develops and promotes measurement standards.
See More...
See Less...
, ISOAn independent, non-governmental international organization that develops and publishes standards.
See More...
See Less...
, etc. |
| Blocked | Blocking is also a valid entry and may be used with a high-scoring sentence such as 'I have blocked the threat actor' |
| Proxy | The idea of proxying network connections, not having someone fill out your bingo card by proxy |
| Network | As it relates to communication on the organization's TCPA connection-oriented communication protocol that ensures data is reliably delivered between computers, with error-checking and guaranteed delivery.
See More...
See Less...
/IP network, whether intranet or internet-based. If used in the context of neural networkA neural network is an AI model inspired by the human brain's structure and function. It consists of layers of interconnected nodes (neurons) that can learn to perform tasks by adjusting the strength of these connections based on data.
See More...
See Less...
then you should complete the Al/Machine Learning square |
| Rule | Typically related to a threat signature or firewall that governs how future occurrences are remediated |
| Recon | Recon or Reconnaissance is good to complete this square. |
| Ticket | Ideally related to a bug tracking system, trouble ticketing system, or service ticketing system. If someone proclaims, 'that's the ticket!' then you probably deserve to complete the square just for being in the same room as that person |
| Threat | Ideally, it relates to network or software threats within the organization. It could also be used in the context of an insider threatA security risk that originates from within the targeted organization, typically involving current or former employees, contractors, or business associates who have inside information concerning the organization's security practices, data, and computer systems. An insider threat can manifest in malicious actions such as theft of proprietary information, sabotage of systems, or data breaches, as well as unintentional actions that inadvertently cause harm or expose sensitive data.
See More...
See Less...
, which hopefully isn't anyone in the room with you right now |
| DNS | It is a pretty straightforward reference to the internet domain name serversA system that translates domain names, like www.example.com, into numerical IP addresses that computers use to identify each other on the network. It functions as the "phone book" of the internet, allowing users to access websites using familiar domain names instead of numerical IP addresses.
See More...
See Less...
, and is likely used as part of a sentence, such as 'I did a DNS lookup on the domain.it was ' |
| Logs | Not of the tree kind, but of the kind typically aggregated from WindowsA series of operating systems developed by Microsoft Corporation. It provides a graphical user interface for managing files and running software applications on computers, laptops, and other devices. Windows is one of the most commonly used operating systems globally.
See More...
See Less...
, LinuxA family of open-source Unix-like operating systems based on the Linux kernel.
See More...
See Less...
, Active-Directory, Firewalls, or other such sources. The term 'Syslog' would be acceptable to complete this square |
| Sorry, I was on mute | You'll likely hear something like this on any internet-based communication software, such as Zoom, Webex, GoToMeeting, etc. Hopefully, never followed by the phrase, "I'm not a cat." |